Why Web Insight™
?
최근 E-Commerce가 급속히 발전함과 동시에 사용자의 개인정보가 유출되거나 기업의 홈페이지 변조,
금융사고등과 같은 해킹사고가 급증하고 있습니다. 이러한 사건들은 대부분 시스템을 직접 해킹하는것이 아니라
누구에게나 개방되어 있는 홈페이지를 통해서 시스템에 침투하는 것입니다. 따라서, 기존의 방화벽이나 IDS,
IPS 등만으로는 이러한 웹해킹을 차단할 수 없게 되었습니다.
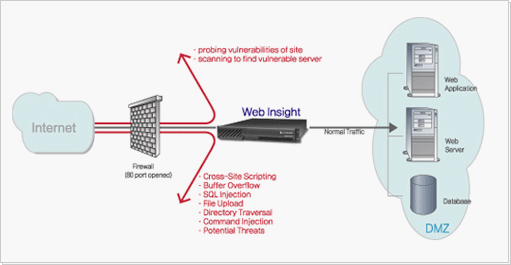
Web을 이용한 공격기법은 꾸준히 발전하면서 증가하고 있습니다. 일반적으로 발생하는 Web을 이용한 공격방법만해도
cross-site scripting, SQL Injection, Buffer overflow를 비롯하여
20여종 되고 공객된 공격은 4,000개이상이고, 알려지지않은 공격을 포함한다면 우리는 항상 나쁜 공격에
대해 불안해 하면서, 그 공격에 대해 준비를 해야만 하고, 무방비 상태에서 공격을 받았을 경우 공개되지않은
payload의 접근이 가능하고, 인가되지 않은 applicaation으로의 접근이 가능하며, Password의
도난, 고객정보의 도난, 고객 데이터의 도난, 데이터의 변형서비스 중단, web-sight 훼손, 데이터
삭제등의 불이익을 당하게 됩니다.
Web Insight™는 이러한 웹 해킹공격에 대해 최고 수준의 해킹차단 서비스를 제공하여 고객의 기업브랜드
이미지제고와 지속적인 수익창출에 도움을 드릴것입니다.
|
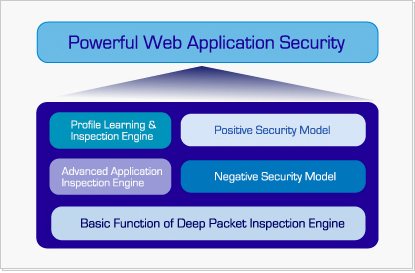
 The Positive Security model
The Positive Security model
Web Insight™는 최초 일정 기간 Learning 과정을 거쳐 웹 서버의 정상적인 통신들을 Profiling화
한 후 클라이언트들의 Request들과 비교하여 정상적이지 않은 Request들은 잠재적인 위협요소로 판단하여
차단합니다.
이러한 Security model은 기존의 Signature-based model과 병행하여 운용함으로써
알려지지 않은 해킹공격으로부터 가장 효과적으로 웹사이트를 보호할 수 있습니다.
 Advan Application Inspection
Advan Application Inspection
Web Insight™의 강력한 Stream Inspection은 현재와 같이 복잡한 웹 환경하에서 기업의
중요한 비즈니스 수단인 웹 사이트의 안전을 폭넓게 보호하여 주는 핵심기능입니다.
Web Insight™는 클라이언트와 웹 서버 사이의 모든 트래픽들을 양방향으로 감시하면서 해킹 공격들을
사전에 차단(Bi-directional Inspection)시킵니다.
모든 Transaction들은 Stream Inspection에 의해 동적으로 검사되어지며, 해킹공격 또는
잠재적인 위협요소들이 나타날시 로그를 기록하고 관리자에게 경고메시지를 통지합니다.
 Strong Prevetion of Information Leakage
Strong Prevetion of Information Leakage
Web Insight™는 Web server가 보유하고 있는 중요한 정보들이 해커에 의해 유출되지 않도록
아래와 같은 다양한 기능들을 제공합니다.
- Web Server Cloaking
- Web server의 response를 조작함으로서 해커의 Web server 분석시도를 사전 에 차단.
- Data Theft Prevention
- 주민등록번호, 신용카드번호 같은 중요한 정보들이 유출되는 것을 차단.
- Error Page Appointment by Administrator
- 해커에 의해 고의적으로 유발된 Error page를 통한 정보유출을 관리자가 Error page를 임의로
지정함으로서 방지.
- Cookie Encryption
- Cookie를 통한 중요정보의 유출을 막기 위해 Cookie를 암호화함.
|
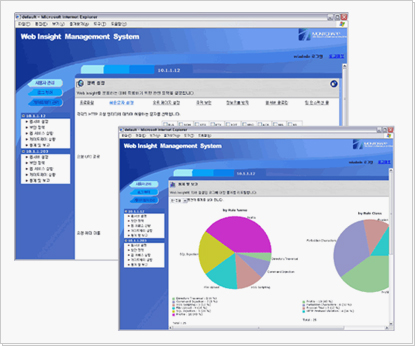
 Efficient Centralized Management
Efficient Centralized Management
중앙의 관리자는 여러 사이트들에 배치된 Web Insight™들을 중앙 Manager를 통해 모든 정책과
관리을 제어하며, 각 사이트의 관리자는 부여된 권한을 바탕으로 임무를 수행합니다.
또한, 관리자들은 Web Insight™의 다양하고 강력한 리포팅 기능들을 통해 보안관련 문제들을 사전에
분석하고 방지할 수 있습니다.
- Health Checking for Gateway
- Use Statistics of web service
- Real time monitoring to chase attacker
- Functions for log searching, analysis and filtering
|

 인사말
인사말  사업분야
사업분야  오시는 길
오시는 길

